🎯 WEEKLY BRIEF
This week brought several fresh bug bounty programs with HIGH payouts and LOW competition! A major AWS supply chain vulnerability showed how small misconfigurations can lead to full cloud takeovers. New CTF’s and labs are kicking off, making it a great time to sharpen your skills. We are also covering a very brief intro to LinPEAS, and a major ransomware breach impacting a key Apple supplier.
🚀 TOP PROGRAMS TO HACK THIS WEEK
Here is YOUR curated list of 5 fresh opportunities to sink your teeth into!
Program | Platform | Asset Type | Max Bounty | Why it’s 🔥 |
HackenProof | Smart Contract | $50,000 ‼️ | Fresh Launch: Started Jan 15; zero reports paid out yet—be the first! | |
Intigriti | Software/ARM | $20,000 | High Impact: Target secure code bases for ARM; great for low-level lovers. | |
HackenProof | Web/Exchange | $5,000 | New Entry: Launched Jan 13; focusing on US-based digital asset security. | |
HackerOne | Hardware/Web | $30,000 ❗ | Massive Scope: Rewards for hardware and cloud assets; very consistent triage. | |
HackerOne | Web/Mobile | $5,000 | Gold Standard: Known for being researcher-friendly with a very wide scope. |
✍️ WRITE UP OF THE WEEK
"CodeBreach: Infiltrating the AWS Console Supply Chain and Hijacking AWS GitHub Repositories via CodeBuild" The Wiz Research Team discovered CodeBreach, a critical vulnerability that allowed a full takeover of the AWS JavaScript SDK.
This exploit targeted a simple misconfiguration, unanchored regex filters in AWS CodeBuild. By missing the ^ and $ anchors, the system only checked if a GitHub User ID contained a trusted ID. The Wiz researches successfully shadowed a maintainers identity by racing to register hundreds of bot accounts until they landed a specific numeric ID that bypassed the filter. This allowed them to trigger privileged builds and extract admin credentials directly from memory.
Full Write Up : CodeBreach (Wiz Blog)

📌 Upcoming Events & CTFs
PascalCTF Beginners 2026: Jan 31 – Feb 1 | Event Info (CTFtime)
Jeanne d'Hack CTF 2026: Jan 30 | Official Site | Event Info (CTFtime)
WUST SOC Lab CTF: Jan–Feb 2026 (Workshops running now) | Official Lab Info
🫛 Tooling & Automation : Intro to LinPEAS
LinPEAS (Linux Privilege Escalation Awesome Script) The industry standard for enumerating Linux privilege escalation vectors. LinPEAS will automatically scan for misconfigured SUID bits, sensitive files, and potential kernel exploits.
Download LinPEAS:
Using cURL:
curl -L https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh -o linpeas.shusing wget:
wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
Make it executable
Linux will not let you run a script you downloaded it until you give it permissions.
chmod +x linpeas.sh
Run and save the results
LinPEAS generates a LOT of text. It is best to run it and save everything to a file so you can read it carefully without it disappearing from your terminal screen.
./linpeas.sh > results.txt
How to read your results:
Once it finishes, open the file (be patient it may take a while):
less -r results.txt
RED/YELLOW: These are almost certainly paths to becoming root. You should check these first. Very likely vulnerabilities
BLUE/GREEN: Information about the system (less urgent).
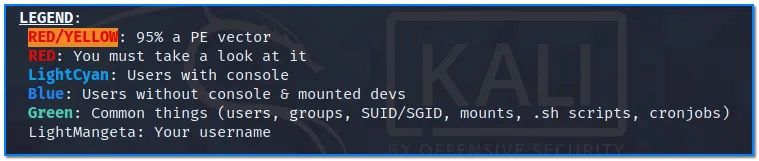
For more documentation and usage of LinPEAS visit these links below!
GitHub Repository: PEASS-ng (LinPEAS)
Usage Guide: LinPEAS Walkthrough (101 Labs)
⚠️ Cyber Attacks
Luxshare Precision (Apple Supplier): On January 20, the extortion group RansomHouse leaked sensitive sample data, including 3D product models and circuit designs for tech giants like Apple and Tesla.
This breach allegedly includes confidential files from 2019 to 2025 and personal details of employees working on secret device architectures.
Experts warn this stolen data could be used by competotors for reverse engineering or by criminals to create high end counterfeit technology.

